October 31, 2017
Why We Need Privacy Tools

If you’re like many individuals, you might not think that you need to use the numerous internet privacy tools currently available. You think you’re relatively safe or you just don’t think about it that much. You share all kinds of information about yourself online. Should you worry? OR, you may be you believe using them means you’re guilty of something that could cause guilt, and that you are hiding something.
The truth is that you don’t need to be a spammer, hacker, or even criminal to want privacy tools. Internet privacy is essential for people for numerous reasons – and for people just like you. It doesn’t matter if you’re a mom of 4 or a high powered executive, a celebrity, a government official, a small business person. All these people come from different perspectives and have different needs but they all have privacy concerns.
There are lots of reasons why you might want to use different privacy-enhancing tools. They will help make sure your rights to privacy and free speech are protected. Your passwords and personal info are secure, protect you from identity theft, safeguard your credit, preserve your relationships. Taking action to protect yourself is a not a universal answer but it’s prudent to take measures where you can. The rights of privacy and free speech are universal to humanity – no matter the country he or she might live in. The Guardian reported in 2014 that 28% of people use some sort of online privacy tool. You probably should too.
But how do people access our private information?

There are many ways our confidentiality can be violated.
Sometimes deleting something really doesn’t mean it’s deleted. You may think more frequently than not that when you delete something the info is removed from the system. This is often not true. There is a lot of trace information which can be left.
What you thought was gone might be found by hackers, and can make you vulnerable. If someone gets access to your computer they can use simple file restoration software to be able to recover the files and then the trouble begins.
This can result in your stolen identity, access to your bank accounts, or some new and unusual charges to your credit card that you didn’t make.
Most web browsers now can save passwords which you visit. Although this feature is useful to us, offenders use and can find this info to access your accounts, internet banking, and credit card balances.
As you browse throughout the internet, many files can end up staying on your PC. Many of those are harmless cookies that allow you to access websites like Amazon.com, but others have a more evil purpose. Spyware can land on your PC, allowing hackers and offenders to track every move you make online.
The Government
How governments handle privacy varies from country to country. A significant event occurred recently in the United States whereby 265 members of Congress passed a law which said that ISPs could sell your data without asking you. Yup, that happened. This is important for a number of reasons but the most important reason is that because you pay for internet service and the ISP can see all of your traffic you should have a right to say how you’re data is used. This is really different from other platforms that may have some of your data because you probably don’t pay for them (Google, Facebook), and they only see some your data and only when you use their platforms and so, in theory, you as the end user are getting “value” out of it and it’s a fair exchange. No matter what side of an issue you fall on your personal and private web traffic history is pretty confidential. Precautions. In. Order. Now.
Another way the government has violated privacy is through literal confiscation. In an article, written recently by Quincy Larson, A native-born American had their cell phone taken away at customs and was held in a locked room until a customs officer demanded his password for his phone. He indicated that there was sensitive data on his device as he was an employee of NASA and was ignored until he provided his password. He was then shortly thereafter released. In that situation, all your data is exposed. This is an extreme example,but it’s clear that protecting yourself is warranted wherever possible.
Malware
Malware is one of the more common ways your information can be compromised. It can result in:
– Loss of data
– The hijacking of your data with it being held ransom,
– Your computer being used for things you’re not aware of
– Hijacking your computer altogether and demanding ransom
– Identity theft
– Adware
It’s pretty nasty stuff. To highlight just how bad malware can be hackers recently included malware into CCleaner, an anti-virus software, which is estimated to have impacted over 2M people.
The whole point with malware is that it’s going to be introduced via something that is benign. A software that’s meant to protect you, an operating system that has not been updated. As Troy Hunt recently said “This is how consumer software these days should be: self-updating with zero input required from the user. As soon as they’re required to do something, it’ll be neglected which is why Windows Update is so critical. Let’s start there:” What this means is that sometimes protection doesn’t have to be hard. It just needs to be turned on. There is no such thing as foolproof but trying is better than not.
Internet Privacy Tools
What are some of the ways you can protect yourself?
Everybody ought to be capable to speak their mind without having to worry whether or not what they are saying is popular or not or may offend some sensibilities.
People should be free to surf the world wide web for information without worrying about being tracked by someone else. Internet privacy tools protect these fundamental human rights. You have the right to freedom of thought so how can you protect yourself from the prying eyes of the digital world.
Some of the things you can do are just simple choices that you can make every day.
A great way to protect yourself is to not allow any cookies to be downloaded to your computer. You can control this in your browser settings. Also, make sure you only visit websites that use HTTPS rather than HTTP and avoid downloading anything from torrent sites as well as adult content sites. Be careful.
You might also want to use a VPN to hide your actual IP address so that you’re browsing history isn’t tracked. VPN stands for virtual private network. The way this works is using a “VPN client” on your computer you connect to the internet through a direct connection to the VPN network and surf the internet through them on your internet connection. This means that the IP that is seen is not your actual IP but an IP address belonging to a VPN network. Something to be conscious about with VPN networks is that a lot of VPNs IP blocks (The IP addresses that VPN services use for their VPN users) are known and blocked anyway from companies who know a little bit about network security. An easy way to get around is running your own VPN server. Here are some examples of privacy tools you can use to protect yourself.
1. Two-Factor Authentication

Passwords aren’t that secure. If someone gets access to your computer and run what’s called a keylogger. They can log all your passwords and then they’ve got a damaging level of access. A great way to protect yourself is with two-factor authentication tools. This isn’t foolproof but it provides a great addition to security by adding a second passcode which changes every 60 seconds. IF anyone is trying to hack you it’s going to get pretty hard for them to do what they need to do in under 60 seconds to get access to your accounts.
2. Copy and Encrypt Your Data
You may not always be able to keep your data secure but maybe you can keep your data intact.
What’s meant by this is that someone may get access to your data but you can keep a version of your data from being affected so that you have a version that is intact and that you’re sure hasn’t been changed that you can refer to for accuracy.
There are lots of different pieces of software which will automatically copy and encrypt your data with a point in time date.
Point in time meaning the copy was made at a specific time and that will tell you whether it may be before or after you’ve been infected or what may be in the data or may be in the data.
3. Use Anti-Malware Software
Clearly, As exemplified in the example above even with the best intentions like running software that is supposed to protect you, you can still be compromised. That said, pick a well-reviewed and widely used software. If for some reason that software is compromised you will be notified thought it can’t hurt to keep your ears to the ground. If the software you are using is compromised switch to something else. Quick action counts for something. Inaction counts more.
4. Don’t Blindly Click on Links
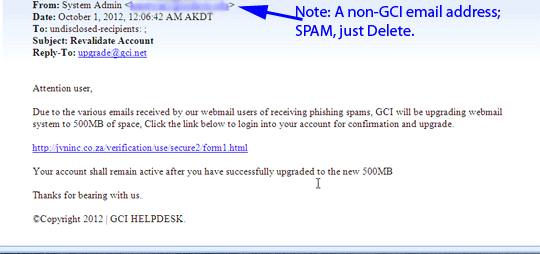
We get targeted with a lot of links. Most of them are harmless but clicking on the wrong link can be a fatal mistake. Luckily there is some basic protection available already right in the browser. If you hover your cursor over a link than in the bottom left corner of the screen the actual full link will appear so you can see and decide if it looks like what it is what you’re being told it is. It looks like a normal domain you’re probably good. IF it looks out of place. Use your judgment to guide your way but use it.
The bottom line is this. There are a lot of problems but you also have lots of options. Quick action counts for something. Inaction counts more.


